Live Chat

Domain Scan

(empty)

Login
Malware Alert*: How to Safeguard Your Hosting Account
(13 - Jun - 2024)

In recent months, a new type of malware has been targeting cPanel hosting accounts. This malware begins its attack by hacking into cPanel accounts, leveraging weak passwords or other vulnerabilities. Once inside, it proliferates by creating files named text.php (although other filenames may also be used) across multiple directories, including critical system directories and user directories. The malware also creates and modifies .htaccess files to maintain its persistence and control over the infected web server.
Malware Behavior
1. Initial Compromise:The attack starts with the hackers gaining unauthorized access to the cPanel account, often through brute force attacks or exploiting weak passwords.
2. File Creation:
Once inside, the malware creates files named text.php in various directories. This includes public directories such as public_html and system directories like root, bin, etc, logs, mail, and php.
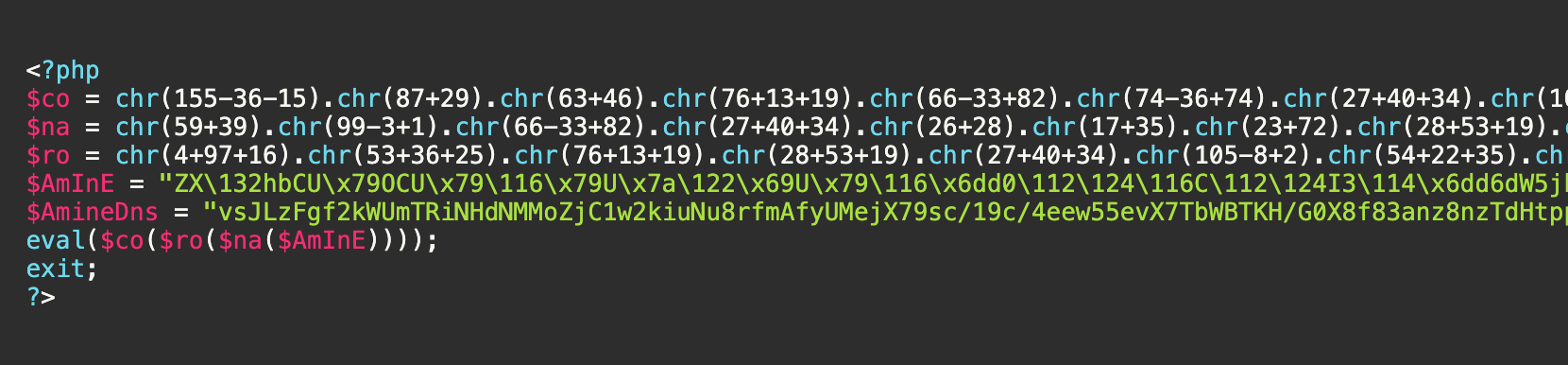
3. Obfuscated Code:
The text.php files contain obfuscated PHP code designed to execute malicious payloads. Here's a sample of such a file:
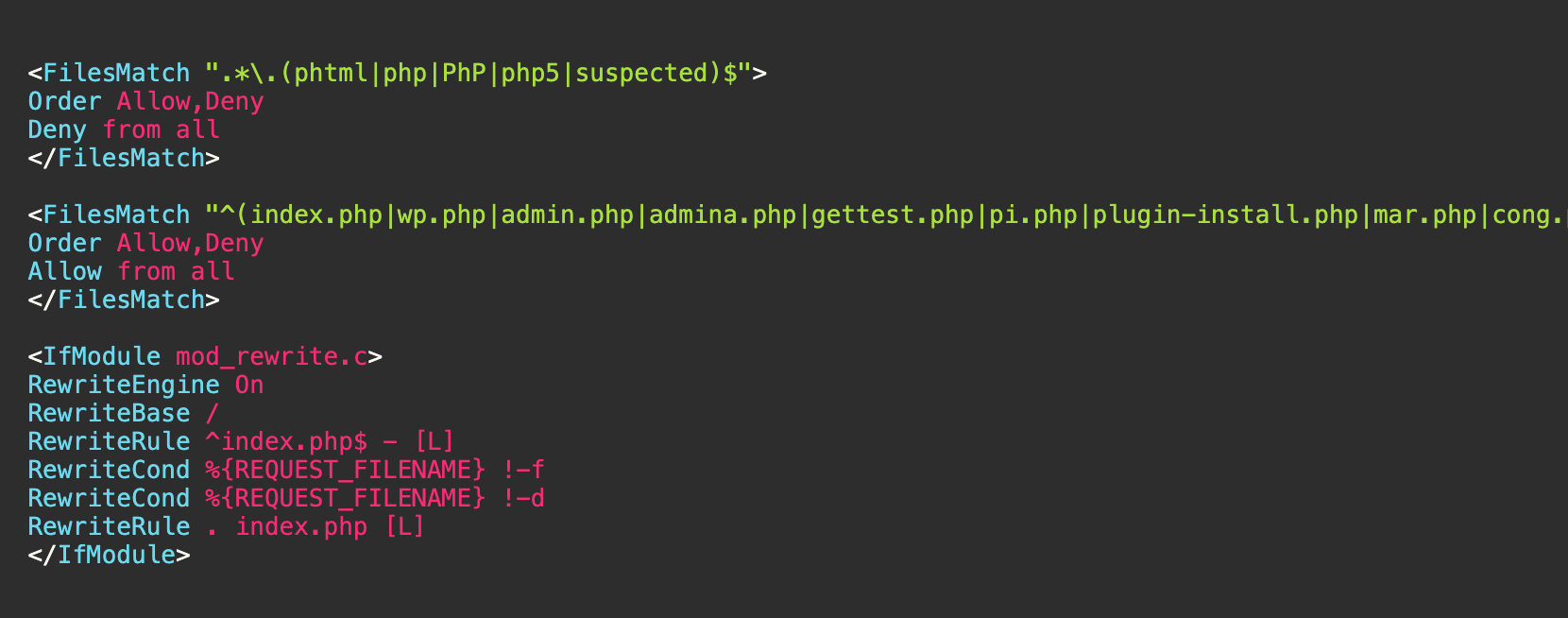
4. .htaccess Modification:
The malware also modifies .htaccess files to deny access to certain file types and allow access to specific files:
5. Additional Malware:
Beyond the initial text.php files, the malware can spread additional types of malware within the public_html directory and other directories. These include various backdoors and injected codes that compromise the security and functionality of the website.
6. File Injection and Modification:
The malware injects malicious code into existing website files, often replacing original code. Commonly affected files include .htaccess and index.php. Once the legitimate code is replaced, recovery becomes difficult without restoring from a backup.
Impact and Recovery
- File Safety: The malicious files created by the malware (such as text.php) can generally be removed without affecting the website's operation, as they are not legitimate website files.- Code Injection: If the malware injects code into existing files, manual removal of the injected code can be attempted. However, if the original code is entirely replaced, restoring from a backup is the only viable option.
- Large-Scale Infections: When the number of infected files exceeds 100, manual recovery becomes impractical. Automated tools or a complete restore from a clean backup are necessary in such cases.
Prevention
To prevent such infections and enhance the security of your cPanel hosting account, consider the following measures:- Strong Passwords: Use complex passwords that combine letters, numbers, and special characters.
- Two-Factor Authentication (2FA): Enable 2FA for an additional layer of security.
- Monitoring and Auditing: Regularly monitor your account and audit files for any unauthorized changes.
By following these security practices, you can significantly reduce the risk of your cPanel hosting account being compromised by this or similar types of malware.
Stay vigilant and proactive in safeguarding your online presence. Protect your cPanel hosting account from emerging threats and ensure the security and integrity of your website today.
 Written by: Register.lk Systems Hero - Lakshani
Written by: Register.lk Systems Hero - Lakshani