Live Chat

Domain Scan

(empty)

Login
Malware Alert*: How to Safeguard Your WordPress Website?
(02-Jul-2024)

Attention all users! A new type of malware has been found targeting WordPress installations across multiple accounts on several of our servers. This security threat was first detected this week and has been affecting multiple cPanel accounts. In this blog post, we will explain the nature of this malware, its behavior, and what you can do to protect your website.
What We Found
The malware was discovered in the wp-config.php file of infected WordPress installations. The malicious code is injected at the very beginning of the file, which is a crucial configuration file for WordPress. The specific code injected includes: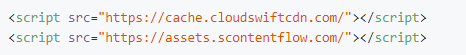 These scripts attempt to load external JavaScript files from the domains cache.cloudswiftcdn.com and assets.scontentflow.com. Upon visiting these URLs, we found complex scripts that incorporate Yandex.Metrica and Matomo (formerly Piwik) Analytics, both of which are legitimate web analytics services. However, their usage in this context is malicious and unauthorized.
These scripts attempt to load external JavaScript files from the domains cache.cloudswiftcdn.com and assets.scontentflow.com. Upon visiting these URLs, we found complex scripts that incorporate Yandex.Metrica and Matomo (formerly Piwik) Analytics, both of which are legitimate web analytics services. However, their usage in this context is malicious and unauthorized.
Understanding the Malicious Code
Here's a detailed breakdown of what the injected code does:1. Loading External Scripts:
- The scripts load additional JavaScript from external sources. These scripts collect detailed user interaction data, including page views, clicks, and user sessions.
- Tracks user clicks, link interactions, and enables the WebVisor feature, which records user sessions.
- Sends tracking data to Yandex.Metrica servers.
- Initializes Matomo to track page views and link clicks.
- Sets the tracker URL and site ID, then loads the Matomo script asynchronously.
Potential Impact on Your Website
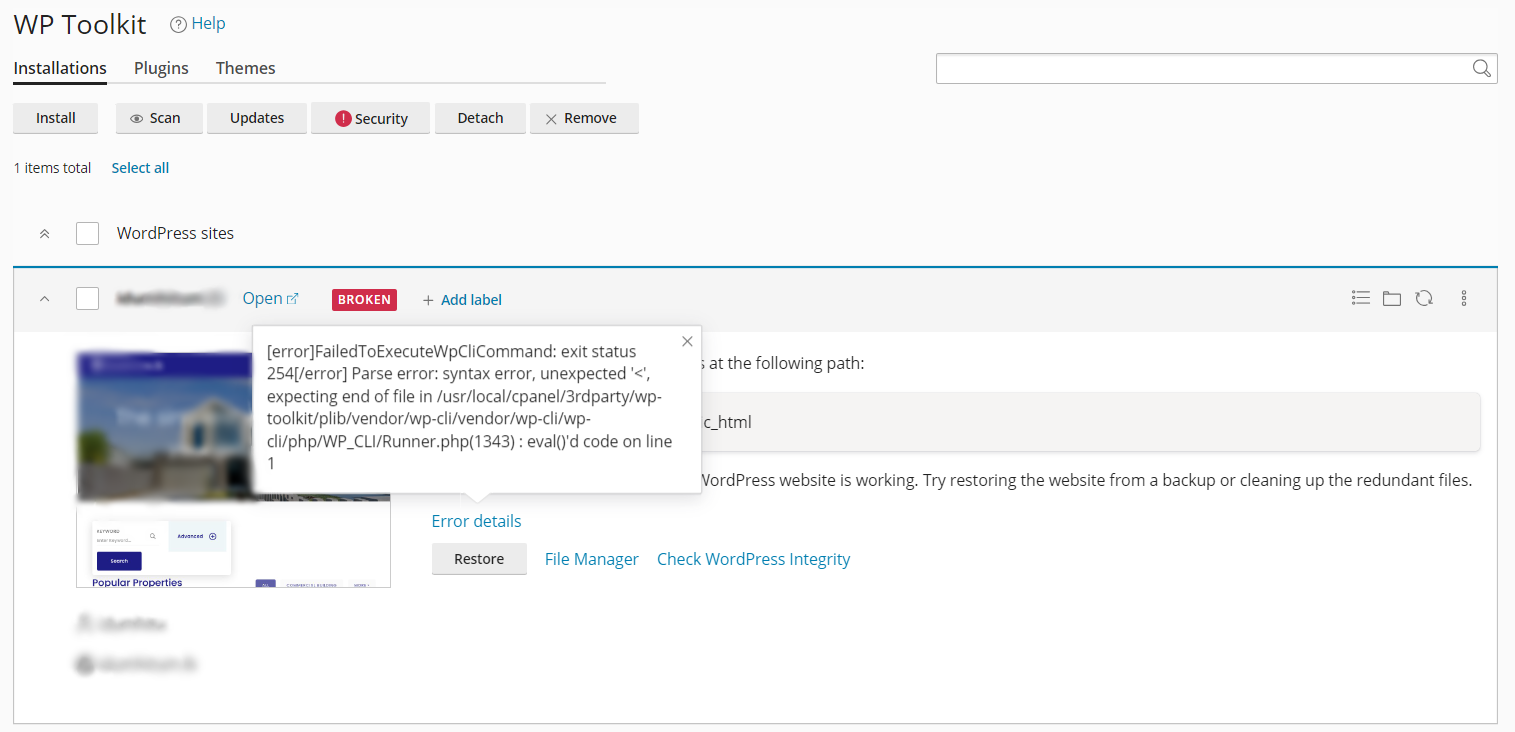
- WP Toolkit Warnings: WP Toolkit will show your site as broken due to the presence of this malicious code. While the website might appear to function normally, the unauthorized scripts can compromise security and user data.
- Privacy Violations: The malware collects user data without consent, posing significant privacy risks.
- Data Leakage: Sensitive user interaction data is sent to external servers, potentially exposing private information.
- Performance Issues: Loading additional scripts can slow down your website, leading to a poor user experience.
- Trust and Reputation: Detection of unauthorized tracking can damage the reputation and trustworthiness of your website.
Immediate Steps to Take
1. Remove the Malicious Code: Check your wp-config.php file for the injected scripts and remove them immediately.2. Conduct a Security Scan: Use a comprehensive security plugin (like Wordfence or Sucuri) to scan your website for additional malware.
3. Update Credentials: Change all relevant passwords, including WordPress admin, database, and FTP credentials.
4. Implement Security Measures:
- Keep WordPress, themes, and plugins updated.
- Use strong, unique passwords.
- Enable two-factor authentication for admin accounts.
- Regularly back up your website and store backups securely.
Enhancing Your Website Security
To prevent future infections, consider the following security enhancements:- Security Plugins: Install and configure security plugins to monitor and protect your site.
- Regular Updates: Keep your WordPress core, themes, and plugins up to date to avoid vulnerabilities.
- Strong Passwords: Use strong, unique passwords and change them regularly.
- Two-Factor Authentication: Enable two-factor authentication for an added layer of security.
- Regular Backups: Regularly back up your website and ensure backups are stored securely.
Conclusion
We take the security of your websites very seriously and are committed to providing the necessary support and resources to keep your data safe. If you suspect your website has been infected or if you need assistance with securing your site, please reach out to our support team immediately.Stay vigilant and proactive in maintaining the security of your online presence.
 Written by: Register.lk Systems Hero - Lakshani
Written by: Register.lk Systems Hero - Lakshani